OPINION: THE FEDERALIST
Broadcasting Board of Governors – Information Warfare: It’s Over, We Lost
BBG: Land of Delusion
By The Federalist
The Broadcasting Board of Governors (BBG) has done a masterful job of placing US Government international broadcasting in virtually a permanent state of being,
- It has dismissed the need for key portions of legislation to enact reform.
- It claims that it needs only one Chief Executive Officer (CEO) to run a multi-tiered organization, having components with separate and distinct missions and a long, long list of systemic problems.
In short, the BBG revels in conducting business as usual when a large share of official Washington shares in a view that the agency is:
- “Dysfunctional” (Heritage Foundation scholar Helle C. Dale)
- “Practically Defunct” (Hillary Clinton)
- “Broken” (US statesmen, diplomats, media experts and journalists interviewed by former BBG member S. Enders Wimbush and former Radio Free Europe / Radio Liberty executive Elizabeth M. Portale)
- “Truly Rudderless” or Leaderless (Chairman of the House Foreign Affairs Committee, Rep. Ed Royce)
The latest condemnation comes again from the House Committee on Foreign Affairs:
“This Broken Agency is Losing the Info War to ISIS & Putin,” House Committee on Foreign Affairs, Chairman Ed Royce, February 23, 2016.
We can now add to this list of the agency’s organizational traits with
- Delusional
Recall if you will a recent claim by the BBG and Alan Heil, a former official from a bygone agency era. Mr. Heil quoted a current BBG member as saying that the agency is “a whirlwind of positive change.”
The claim is bogus. But it is typical for an agency that has long gotten away with other bogus, unilateral declarations of imagined success or effectiveness. It has gotten so bad that we can now label the BBG as
“The Land of Delusion.”
Adding to the delusion is a recent article appearing on the FederalNewsRadio.com website:
“Broadcasting Board of Governors kicked the Chinese out of its network, remains vigilant as cyber attacks continue.”
You can read the article here.
Right from the get-go, the article starts off with the declaration,
“The Broadcasting Board of Governors is free from the grasp of Chinese hackers.”
Reality paints a far different picture: and that reality is likely to mean that the agency has not yet detected whatever intrusions may already be in its IT systems, courtesy of the Chinese.
The star of the show in this piece is Andre Mendes.
Here is why this article is a really bad decision to put self-promotion ahead of agency cyber security.
When reading the article, Mr. Mendes cannot contain his exuberance to detail what the agency is doing in the way of cyber countermeasures to attempted Chinese intrusions.
“When I first came on board in 2009, every single server in this agency was controlled by the Chinese cyber army and they could have literally dropped this agency with one key stroke. Fortunately they chose never to do so, but at the same time we knew they were exfiltrating literally gigabyte upon gigabyte of information every day.”
If that is true, at what point did Mr. Mendes and the agency warn BBG employees that their personal data was being compromised?
But these revelations from Mr. Mendes have created an even bigger problem now. Perhaps it has escaped the attention of Mr. Mendes and the BBG that the Chinese have more than likely read the article. Now they know what the agency is doing and no doubt have intended strategies to prove Mr. Mendes wrong.
Mr. Mendes himself admits in the article, “We have far too many, far too sophisticated people that are really trying to get into our data centers and wreak havoc with our operations.”
What that means is that hostile cyber warfare specialists are likely to far exceed the assumed “brain trust” of the BBG. And these adversaries are persistent.
Even if Mr. Mendes’ statement were to be true, it is not a permanent condition. It is temporary and illusory because cyber warfare is constantly evolving. More than once, we have seen instances in which Federal agencies have been compromised by state-sponsored cyber warfare or that of non-state criminal enterprises.
In so many words, the BBG is child’s play in the big picture of cyber warfare. Even if there is the appearance that the agency has had former successes, it is not a guarantee for the present or future. The Chinese have a strategic vision, a chess match if you will, in which creating a false sense of security is an active component. Making the mistake of bragging about past successes in cyber countermeasures opens the door for setting up future attacks.
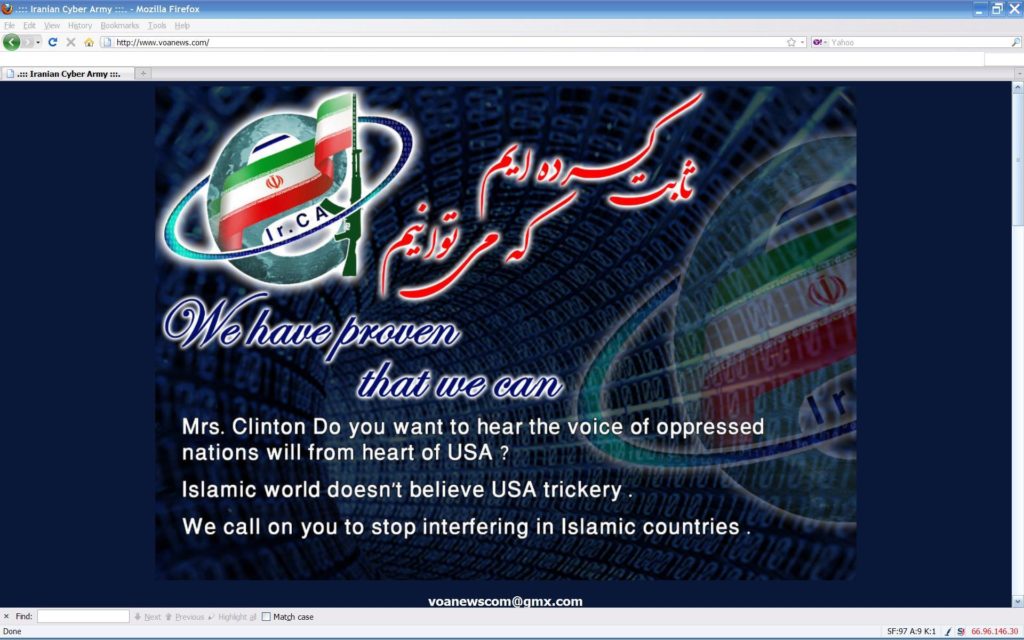
The Federal News Radio article makes no mention of the successful Iranian Cyber Army hacking of the VOA website, repeated failures of digital storage and audio and video processing infrastructure used by VOA reporters, and a recent power failure which IBB was unable to fix for many hours and which prevented VOA programs from being transmitted to their audiences abroad.
This was reported earlier by BBG Watch:
The Iranian Cyber Army managed to launch a successful hacking attack on the Voice of America (VOA) main news website in February 2011, replacing it for several hours with and anti-U.S. message addressed to the then Secretary of State Hillary Clinton.
The Federal News Radio article also does not mention that the Broadcasting Board of Governors’ response to cybersecurity incidents and its newly developed policy and procedures were the subject of a cutting review by auditors at Williams, Adley & Company-DC, as pointed out by the agency’s Inspector General in a new report and reported by Aaron Boyd, Senior Staff Writer, Federal Times, on January 20, 2016: “IG: Broadcasting Board cyber policies not ready for primetime.”
According to an earlier 2014 Office of Inspector General (OIG) audit, the Broadcasting Board of Governors Information Security Program showed “a significant deficiency.”
We should also compare Mr. Mendes’ self-congratulatory remarks in the context of a recent article in The Washington Post reviewing a new book by author Fred Kaplan (“The Secret History of Cyber War,” Simon and Schuster). The article itself can be read here.
The author of the review is Gordon Goldstein, a managing director at the global technology investment firm Silver Lake Partners and an adjunct senior fellow at the Council on Foreign Relations.
Particularly relevant to our discussion are passages in Kaplan’s book as noted by Mr. Goldstein:
“The cyberthreat posed by China is among the most acute, Kaplan observes, because it is driven by a diverse spectrum of incentives…”
“The principal Chinese antagonist…was well known across the senior ranks of the Obama administration. It was the Second Bureau of the Third Department of the People’s Liberation Army’s General Staff, also known as Unit 61398, headquartered in a 12-story building outside Shanghai. It is but one cadre of a cyber force estimated to be in the tens of thousands.” (emphasis added)
And how many people does Mr. Mendes have in his cyber force?
And what kind of budget does Mr. Mendes have in comparison to the likely fiscal commitment by the Chinese?
Who is Mr. Mendes kidding, besides himself?
“Diverse spectrum of incentives.” Surely, there are incentives for the Chinese not to cut Mendes and the BBG any slack: for example, emails and other data pointing to Chinese dissidents are valuable to the Chinese government which places a high priority on control and stability of its political environment. And here we have Mr. Mendes, quite incapable of containing himself, taunting the People’s Liberation Army.
We have a word for this:
Foolish.
It is yet another “victory” of personal egotism over judgment.
As we have noted: Mr. Mendes and the BBG are child’s play for the resources of the Chinese and the People’s Liberation Army. At a time and place of their choosing, we can almost certainly guarantee that they will remind both Mr. Mendes and the BBG of their folly.
That’s another thing: Mr. Mendes does not distinguish between activity and capability. What the Chinese like to do is milk a data source for information, do so until discovered and if blocked after the fact, develop new avenues of approach. One compares this to the Russians who often approach cyber warfare more aggressively to do actual damage and not be content with just mining a data source. At the same time, one should be wary of what capabilities the Chinese have but have not deployed.
And by the way, the Chinese are also most likely aware of the recent meltdown of Mr. Mendes’ IT infrastructure. They would have to be amused by Mendes’ bragging of blocking them while he can’t keep his own domain of IT hardware and software running even without any external intrusion.
We are also reminded that Mr. Mendes “promised” a full accounting of what happened. We haven’t seen it, if it exists at all. As the Chinese might be inclined to remark on the workings of the BBG,
“Consider the source.”
The Federalist
April 2016