Federal News Radio
Andre Mendez, BBG CIO and CTO
“When I first came on board in 2009, every single server in this agency was controlled by the Chinese cyber army and they could have literally dropped this agency with one key stroke. Fortunately they chose never to do so, but at the same time we knew they were exfiltrating literally gigabyte upon gigabyte of information every day,” said Andre Mendes, the chief information officer and CTO of the Broadcasting Board of Governors. “We were able to eradicate them through a long-term exercise, about four months, to completely clean them out of our environment, but we continue to be targets for some of the most sophisticated cyber hackers in the world.”
See more: Broadcasting Board of Governors kicked the Chinese out of its network, remains vigilant as cyber attacks continue, By Jason Miller, Federal News Radio, April 15, 2016
New Voice of America director Amanda Bennett should question all BBG bureaucracy PR claims, especially if they come from the International Broadcasting Bureau (IBB), BBG Watch commented.
A recent article in Federal News Radio, “Broadcasting Board of Governors kicked the Chinese out of its network, remains vigilant as cyber attacks continue” is a perfect example of BBG PR fed to U.S. media. Andre Mendes, the chief information officer and CTO of the Broadcasting Board of Governors, makes claims which based on IBB’s performance record so far are highly suspect because they omit critical material facts.
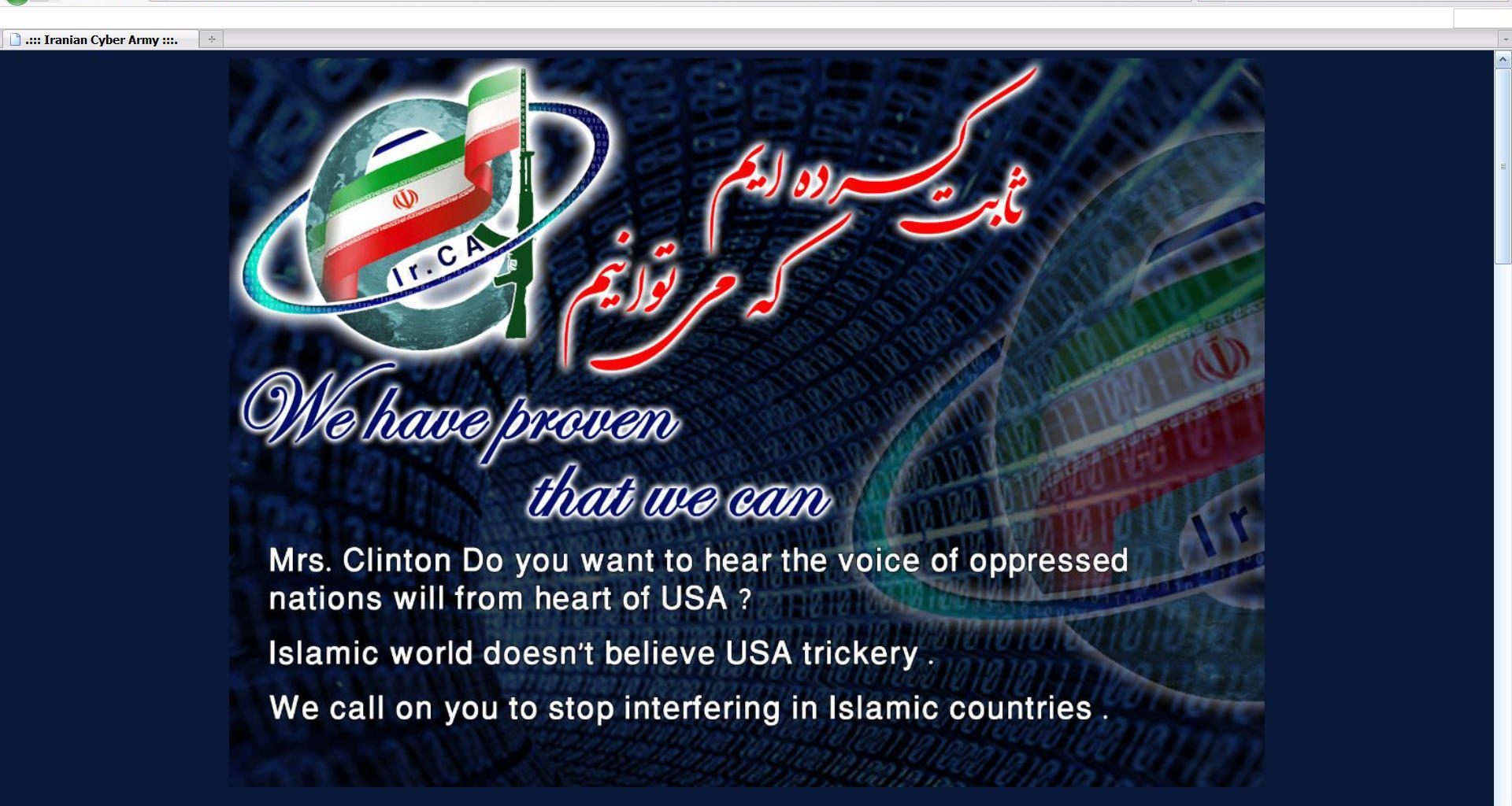
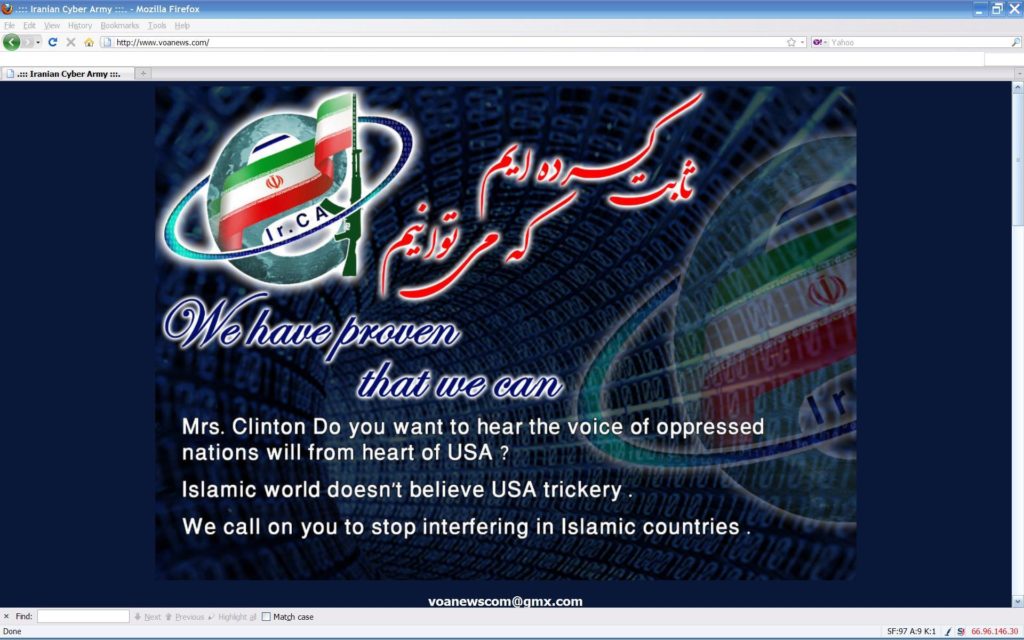
The Federal News Radio article makes no mention of the successful Iranian Cyber Army hacking of the VOA website, repeated failures of digital storage and audio and video processing infrastructure used by VOA reporters, and a recent power failure which IBB was unable to fix for many hours and which prevented VOA programs from being transmitted to their audiences abroad.
The Iranian Cyber Army managed to launch a successful hacking attack on the Voice of America (VOA) main news website in February 2011, replacing it for several hours with and anti-U.S. message addressed to the then Secretary of State Hillary Clinton.
The Federal News Radio article also does not mention that the Broadcasting Board of Governors’ response to cybersecurity incidents and its newly developed policy and procedures were the subject of a cutting review by auditors at Williams, Adley & Company-DC, as pointed out by the agency’s Inspector General in a new report and reported by Aaron Boyd, Senior Staff Writer, Federal Times, on January 20, 2016: “IG: Broadcasting Board cyber policies not ready for primetime.”
According to an earlier 2014 Office of Inspector General (OIG) audit, the Broadcasting Board of Governors Information Security Program showed “a significant deficiency.”
OIG: “Collectively, the information security control weaknesses we identified in this audit represent a significant deficiency to enterprise-wide security, as defined by OMB Memorandum M-14-04.3 We identified control weaknesses in 9 of the 11 information security program areas that considerably impacted BBG’s information security program. The most significant information security deficiencies are related to the risk management framework, continuous monitoring program, [Redacted] (b) (5)  contingency plans, configuration management, and the incident response and reporting program. In addition, information security program areas that need improvement include Plans of Action and Milestones (POA&M), remote access, identity and access management, and security training. Since FY 2010, the weak (and in some cases lack of) security controls adversely affected the confidentiality, integrity, and availability of information and information systems. As an example, according to a BBG official, the weak security controls resulted in the hacking of BBG Web sites in 2011.”
Comments are closed.